The Identity Layer for Real, Monetisable Growth
Growth in Web3 is broken. Glyph fixes it — privately.
Private by design, powered by zero knowledge proofs.
Take control of how you’re seen in Web3.
Wallets Aren’t Users. Identity Is Fragmented.
Billions of addresses move value every day, but teams can’t reliably link them to a single user, de-duplicate participation, or measure the behaviors that actually matter.
Users operate across multiple wallets and chains — UX, attribution, and segmentation break. → fragmented experience.
Sybil wallets farm rewards, airdrops, and governance → incentives get hijacked.
No portable identity means one-off transactions → retention and loyalty don’t compound.
Growth spend leaks into unverifiable activity → targeting, measurement, and ROI stay noisy.
Grant → Scope
activity.last30d
Proof Bundle → Merkle
paths + SNARK
Client Verify → WASM
SNARK vk
on‑chain read
Zero / Minimal gas
Proofs, Not Profiles.
Glyph lets apps verify specific facts about a user without exposing wallets or building a dossier. Only what’s consented gets revealed - nothing more.
Zero‑Knowledge Proofs
Prove predicates without revealing wallets, balances, or history.
Consent Grants
Per-app scopes, expiries, and revocation - controlled by the user.
Per‑App Nullifiers
Sybil-resistant and unlinkable across
apps by default.
Unified ID
on-chain

Identity 1

Identity 2

Identity 3

Identity 4

Identity 5
Decentralized Social Platforms

NFT Marketplace
DeFi Platform
Consent Gated Reads
// frontend.js (browser)
import { ethers } from "ethers";
async function requestConsent() {
if (!window.ethereum) throw new Error("Wallet not found");
const address = await signer.getAddress();
await fetch("/api/c
User Wallets &
Attributes
grouped into an on-chain identity graph
Relayer network
powered by zk proofs and per app nullifiers
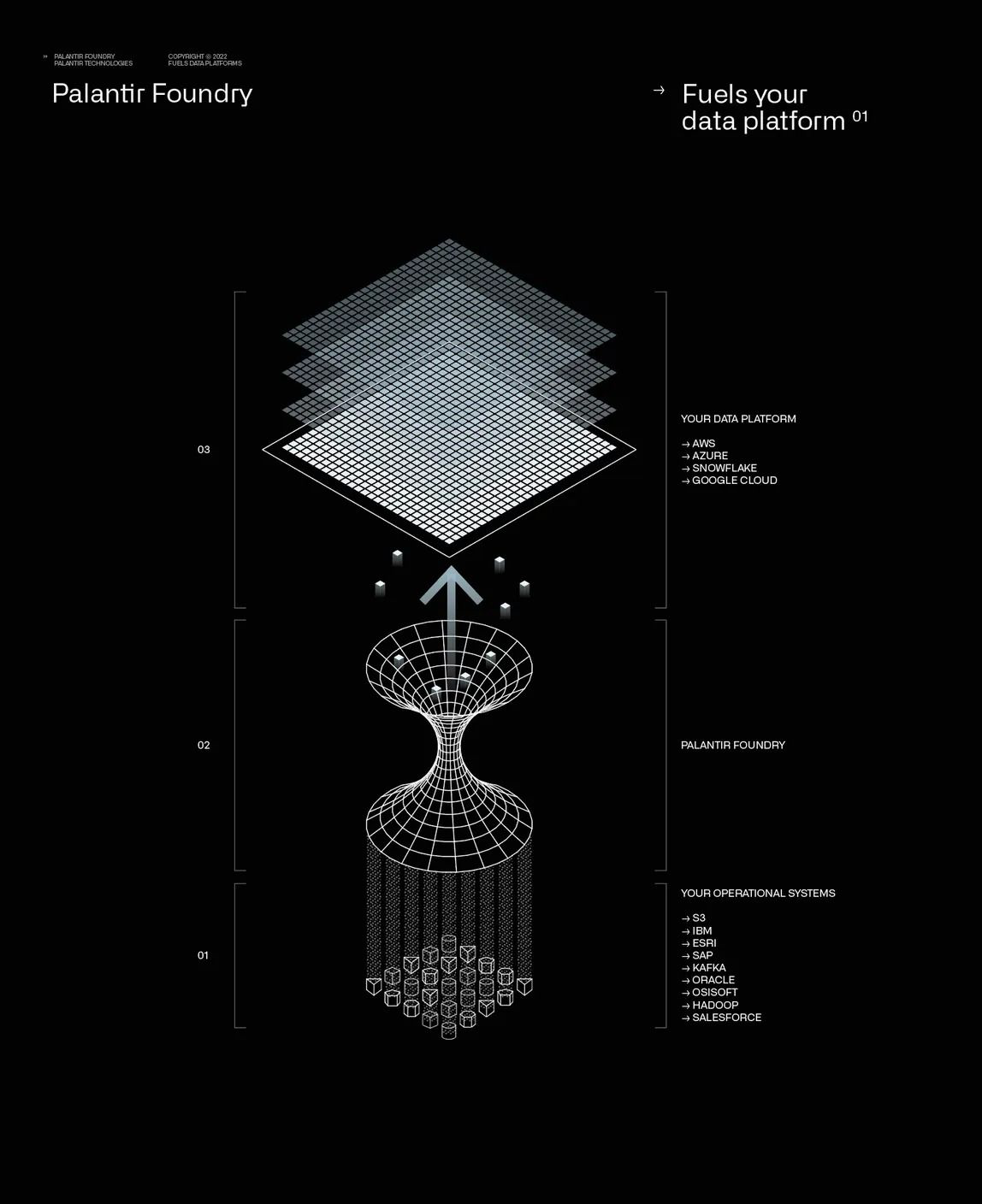
UnifiedID Graph + Relayer Network
UnifiedID
User-owned identity graph (ZK-friendly Merkle tree) that links wallets (and optional attributes) across chains. Apps verify facts, the graph stays private. Only a root commitment needs to touch chain.
Selective disclosure (facts like “active_30d”, not wallet sets).
Scoped grants per app; revocation bumps epoch/root.
Optional attribute proofs (e.g., age ≥ 18) with selective disclosure.
Relayer Network
Permissionless, staked executors that run identity jobs across chains - with commit-reveal, deterministic slashing, and challenge bounties to keep proofs honest.
Stake → Quote → Execute → Prove → Settle → Challenge window.
Fee vaults with protocol rake; QoS bonuses; unbonding periods.
Challengers rewarded for evidence‑based slashes.

Consent Gated Reads
// frontend.js (browser)
import { ethers } from "ethers";
Relayer network
powered by zk proofs and per app nullifiers
Claim Playground
Generate a scoped claim and verify it locally.
Copy code
Relayer Explorer & Challenge Board
Observe network throughput, latency distributions, recent jobs, and evidence‑based slashes.
From Identity to Utility
Developer Stack
SDKs & APIs for client-side verification (WASM verifier, proofs-as-payload).
Quickstarts: prebuilt proof templates for common claims (active_30d, human, repeat_user).
Relayer tooling: run a node, monitor SLOs, earn fees for identity jobs.
Business KPIs
Key business metrics and performance indicators
TVL by Protocol
Lending
$1794.6M
-0.7%
Staking
$897.3M
+3.8%
Liquidity Pools
$200.1M
-0.8%
16000
12000
8000
4000
0
2025-08-27
2025-08-29
2025-08-31
2025-09-02
2025-09-04
2025-09-006
2025-08-27
swap : 14406
deposit : 6755
take : 4223
unstake : 2952
Health
8/10
Overall
Action Breakdown
Business Health Breakdown
Growth
8.3
Retention
7.2
Revenue
8.1
Risk
6.8
SITA9 — Identity‑Aware Growth
Cohorts & personas from verified behavior.
Churn/LTV models with uplift tracking and A/B guardrails.
AI recommendations for incentive design and allocation.
Business KPIs
Key business metrics and performance indicators
TVL by Protocol
Lending
$1794.6M
-0.7%
Staking
$897.3M
+3.8%
Liquidity Pools
$200.1M
-0.8%
16000
12000
8000
4000
0
2025-08-27
2025-08-29
2025-08-31
2025-09-02
2025-09-04
2025-09-006
2025-08-27
swap : 14406
deposit : 6755
take : 4223
unstake : 2952
Health
8/10
Overall
Action Breakdown
Business Health Breakdown
Growth
8.3
Retention
7.2
Revenue
8.1
Risk
6.8
Our Partners
The Network of Trust
Glyph turns fragmented wallets into verifiable users — with ZK proofs, consent scopes, and sybil-resistant execution. Less leakage. More signal. Compounding trust.
Copyright 2026 © Glyph | All rights reserved | Whitepaper
Read Whitepaper
Docs
Get UnifiedID
The Identity Layer for Real, Monetisable Growth
Growth in Web3 is broken. Glyph fixes it — privately.
Private by design, powered by zero knowledge proofs.
Take control of how you’re seen in Web3.
Home
Home
Home
Wallets Aren’t Users. Identity Is Fragmented.
Billions of addresses move value every day, but teams can’t reliably link them to a single user, de-duplicate participation, or measure the behaviors that actually matter.
Users operate across multiple wallets and chains — UX, attribution, and segmentation break. → fragmented experience.
Sybil wallets farm rewards, airdrops, and governance → incentives get hijacked.
No portable identity means one-off transactions → retention and loyalty don’t compound.
Growth spend leaks into unverifiable activity → targeting, measurement, and ROI stay noisy.
Grant → Scope
activity.last30d
Proof Bundle → Merkle
paths + SNARK
Client Verify → WASM
SNARK vk
on‑chain read
Zero / Minimal gas
Proofs, Not Profiles.
Glyph lets apps verify specific facts about a user without exposing wallets or building a dossier. Only what’s consented gets revealed - nothing more.
Zero‑Knowledge Proofs
Prove predicates without revealing wallets, balances, or history.
Consent Grants
Per-app scopes, expiries, and revocation - controlled by the user.
Per‑App Nullifiers
Sybil-resistant and unlinkable across
apps by default.
Unified ID
on-chain

Identity 1

Identity 2

Identity 3

Identity 4

Identity 5
Decentralized Social Platforms

NFT Marketplace
DeFi Platform
Consent Gated Reads
// frontend.js (browser)
import { ethers } from "ethers";
async function requestConsent() {
if (!window.ethereum) throw new Error("Wallet not found");
const address = await signer.getAddress();
await fetch("/api/c
User Wallets &
Attributes
grouped into an on-chain identity graph
Relayer network
powered by zk proofs and per app nullifiers
UnifiedID Graph + Relayer Network
UnifiedID
User-owned identity graph (ZK-friendly Merkle tree) that links wallets (and optional attributes) across chains. Apps verify facts, the graph stays private. Only a root commitment needs to touch chain.
Selective disclosure (facts like “active_30d”, not wallet sets).
Scoped grants per app; revocation bumps epoch/root.
Optional attribute proofs (e.g., age ≥ 18) with selective disclosure.
Relayer Network
Permissionless, staked executors that run identity jobs across chains - with commit-reveal, deterministic slashing, and challenge bounties to keep proofs honest.
Stake → Quote → Execute → Prove → Settle → Challenge window.
Fee vaults with protocol rake; QoS bonuses; unbonding periods.
Challengers rewarded for evidence‑based slashes.

Consent Gated Reads
// frontend.js (browser)
import { ethers } from "ethers";
Relayer network
powered by zk proofs and per app nullifiers
Claim Playground
Generate a scoped claim and verify it locally.
Copy code

Relayer Explorer & Challenge Board
Observe network throughput, latency distributions, recent jobs, and evidence‑based slashes.
From Identity to Utility
Developer Stack
SDKs & APIs for client-side verification (WASM verifier, proofs-as-payload).
Quickstarts: prebuilt proof templates for common claims (active_30d, human, repeat_user).
Relayer tooling: run a node, monitor SLOs, earn fees for identity jobs.
Business KPIs
Key business metrics and performance indicators
TVL by Protocol
Lending
$1794.6M
-0.7%
Staking
$897.3M
+3.8%
Liquidity Pools
$200.1M
-0.8%
16000
12000
8000
4000
0
2025-08-27
2025-08-29
2025-08-31
2025-09-02
2025-09-04
2025-09-006
2025-08-27
swap : 14406
deposit : 6755
take : 4223
unstake : 2952
Health
8/10
Overall
Action Breakdown
Business Health Breakdown
Growth
8.3
Retention
7.2
Revenue
8.1
Risk
6.8
SITA9 — Identity‑Aware Growth
Cohorts & personas from verified behavior.
Churn/LTV models with uplift tracking and A/B guardrails.
AI recommendations for incentive design and allocation.
Business KPIs
Key business metrics and performance indicators
TVL by Protocol
Lending
$1794.6M
-0.7%
Staking
$897.3M
+3.8%
Liquidity Pools
$200.1M
-0.8%
16000
12000
8000
4000
0
2025-08-27
2025-08-29
2025-08-31
2025-09-02
2025-09-04
2025-09-006
2025-08-27
swap : 14406
deposit : 6755
take : 4223
unstake : 2952
Health
8/10
Overall
Action Breakdown
Business Health Breakdown
Growth
8.3
Retention
7.2
Revenue
8.1
Risk
6.8
Our Partners
The Network of Trust
Glyph turns fragmented wallets into verifiable users — with ZK proofs, consent scopes, and sybil-resistant execution. Less leakage. More signal. Compounding trust.
Copyright 2026 © Glyph | All rights reserved | Whitepaper
Read Whitepaper
Documentation
Get UnifiedID
The Identity Layer for Real, Monetisable Growth
Growth in Web3 is broken. Glyph fixes it — privately.
Private by design, powered by zero knowledge proofs.
Take control of how you’re seen in Web3.
Home
Home
Home
Wallets Aren’t Users. Identity Is Fragmented.
Billions of addresses move value every day, but teams can’t reliably link them to a single user, de-duplicate participation, or measure the behaviors that actually matter.
Users operate across multiple wallets and chains → UX and segmentation break.
Sybil wallets farm rewards, airdrops, and governance → incentives get hijacked.
No portable identity means one-off transactions → retention and loyalty don’t compound.
Growth spend leaks into unverifiable activity → targeting, measurement, and ROI stay noisy.
Grant → Scope
activity.last30d
Proof Bundle → Merkle
paths + SNARK
Client Verify → WASM
SNARK vk
on‑chain read
Zero / Minimal gas
Proofs, Not Profiles.
Glyph lets apps verify specific facts about a user without exposing wallets or building a dossier. Only what’s consented gets revealed - nothing more.
Zero‑Knowledge Proofs
Prove predicates without revealing wallets, balances, or history.
Consent Grants
Per-app scopes, expiries, and revocation - controlled by the user.
Per‑App Nullifiers
Sybil-resistant and unlinkable across
apps by default.
Unified ID
on-chain

Identity 1

Identity 2

Identity 3

Identity 4

Identity 5
Consent Gated Reads
// frontend.js (browser)
import { ethers } from "ethers";
async function requestConsent() {
if (!window.ethereum) throw new Error("Wallet not found");
const address = await signer.getAddress();
await fetch("/api/c
User Wallets &
Attributes
grouped into an on-chain identity graph
Relayer network
powered by zk proofs and per app nullifiers
UnifiedID Graph + Relayer Network
UnifiedID
User-owned identity graph (ZK-friendly Merkle tree) that links wallets (and optional attributes) across chains. Apps verify facts, the graph stays private. Only a root commitment needs to touch chain.
Selective disclosure (facts like “active_30d”, not wallet sets).
Scoped grants per app; revocation bumps epoch/root.
Optional attribute proofs (e.g., age ≥ 18) with selective disclosure.
Relayer Network
Permissionless, staked executors that run identity jobs across chains - with commit-reveal, deterministic slashing, and challenge bounties to keep proofs honest.
Stake → Quote → Execute → Prove → Settle → Challenge window.
Fee vaults with protocol rake; QoS bonuses; unbonding periods.
Challengers rewarded for evidence‑based slashes.

Consent Gated Reads
// frontend.js (browser)
import { ethers } from "ethers";
Relayer network
powered by zk proofs and per app nullifiers
Claim Playground
Generate a scoped claim and verify it locally.
Copy code

Relayer Explorer & Challenge Board
Observe network throughput, latency distributions, recent jobs, and evidence‑based slashes.
From Identity to Utility
Developer Stack
SDKs & APIs for client-side verification (WASM verifier, proofs-as-payload).
Quickstarts: prebuilt proof templates for common claims (active_30d, human, repeat_user).
Relayer tooling: run a node, monitor SLOs, earn fees for identity jobs.
Business KPIs
Key business metrics and performance indicators
TVL by Protocol
Lending
$1794.6M
-0.7%
Staking
$897.3M
+3.8%
Liquidity Pools
$200.1M
-0.8%
16000
12000
8000
4000
0
2025-08-27
2025-08-29
2025-08-31
2025-09-02
2025-09-04
2025-09-006
2025-08-27
swap : 14406
deposit : 6755
take : 4223
unstake : 2952
Health
8/10
Overall
Action Breakdown
Business Health Breakdown
Growth
8.3
Retention
7.2
Revenue
8.1
Risk
6.8
SITA9 — Identity‑Aware Growth
Cohorts & personas from verified behavior.
Churn/LTV models with uplift tracking and A/B guardrails.
AI recommendations for incentive design and allocation.
Business KPIs
Key business metrics and performance indicators
TVL by Protocol
Lending
$1794.6M
-0.7%
Staking
$897.3M
+3.8%
Liquidity Pools
$200.1M
-0.8%
16000
12000
8000
4000
0
2025-08-27
2025-08-29
2025-08-31
2025-09-02
2025-09-04
2025-09-006
2025-08-27
swap : 14406
deposit : 6755
take : 4223
unstake : 2952
Health
8/10
Overall
Action Breakdown
Business Health Breakdown
Growth
8.3
Retention
7.2
Revenue
8.1
Risk
6.8
Our Partners
The Network of Trust
Glyph turns fragmented wallets into verifiable users — with ZK proofs, consent scopes, and sybil-resistant execution. Less leakage. More signal. Compounding trust.
Copyright 2026 © Glyph | All rights reserved | Whitepaper